We recently had the need to establish a Site to Site VPN connection with our Meraki MX65w security appliance. Meraki security appliances have the option to establish a Site to Site VPN connection to other security appliances as well as other third-party routers. In our scenario, we successfully configured a connection between our security appliance and a Cisco RV325. Configuring the Site to Site VPN on the security appliance is well documented by Meraki. This documentation can be found in the link below.
https://documentation.meraki.com/MX-Z/Site-to-site_VPN/Site-to-site_VPN_Settings
Unfortunately, there is no documentation with configuring this connection specifically with a Cisco RV325. Our initial attempts were unsuccessful and upon examining the logs we found we kept receiving the same error message “phase 1 failed due to time up.” Upon researching into this error, we stumbled upon documentation from Meraki entitled “Troubleshooting Site to Site VPN Connections with Non-Meraki Peers” (link below).
This article had a description of the error messages and a proposed solution. Unfortunately for us, the solution provided for our problem was generic and not very useful. As a result, it forced us to escalate this issue with Meraki support and do a scheduled call. Meraki support had access to our cloud configuration and could troubleshoot the issue by examining logs and performing a packet capture on the inbound traffic to our MX65w. The support was very useful and we had the issue resolved very promptly.
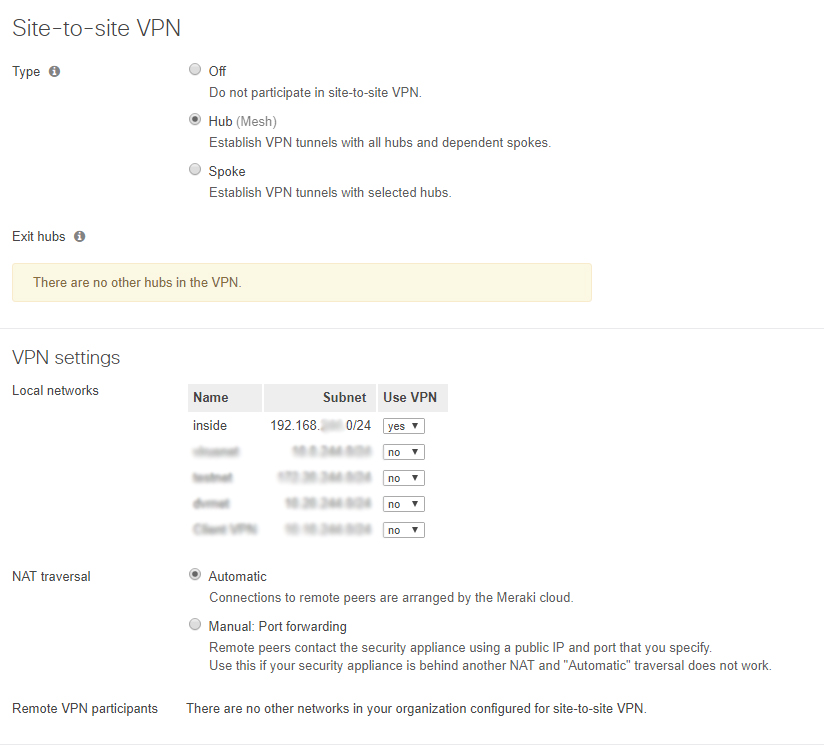
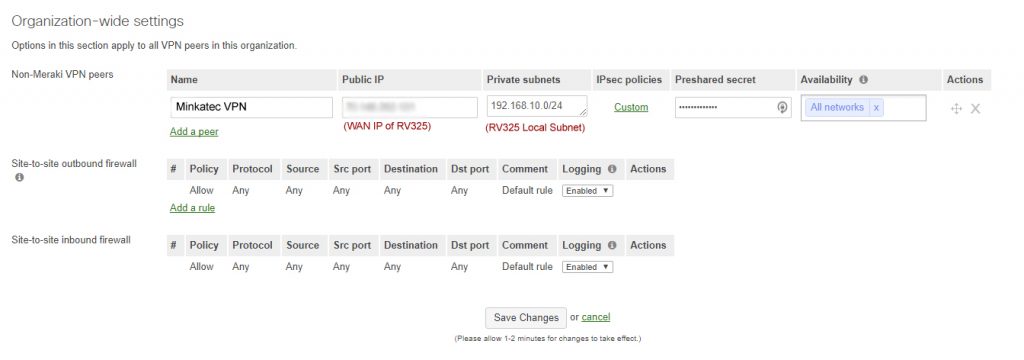
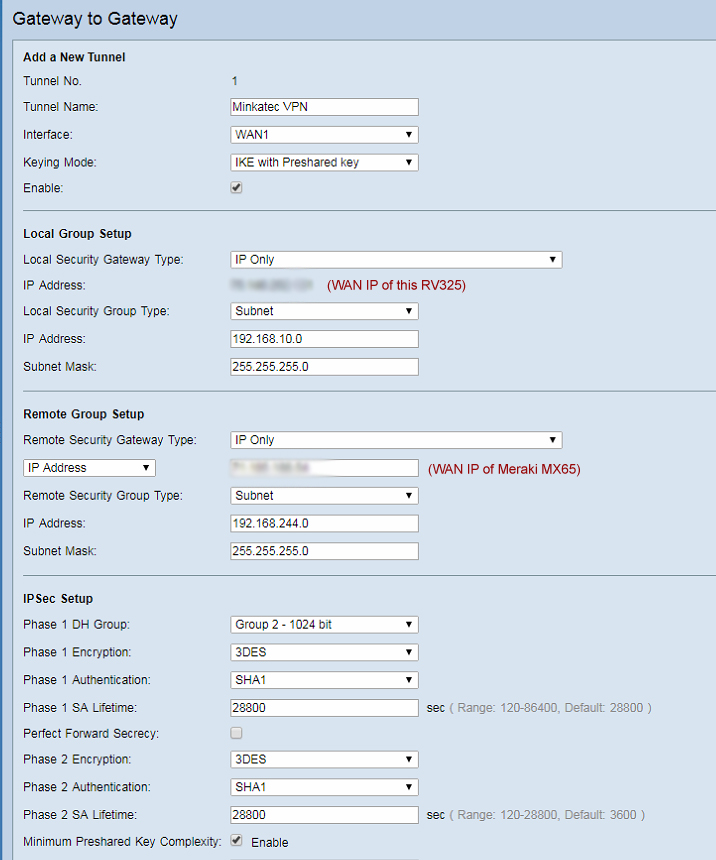
Below are our settings for a successful Site to Site VPN connection between these two devices.
The Meraki Mx65w provides the ability to pass multiple subnets over the VPN which can be configured with the Use VPN yes/no drop down menu. In our scenario, we are only passing through one subnet.
By default, both devices allow all traffic over the VPN unless configured otherwise. Meraki does not allow the configuration of inbound firewall rules over the VPN and allows all traffic. Hopefully this feature will be allowed in the future as sometimes you might not have access to both devices and only want to allow certain inbound traffic through the VPN. With the current inbound allow all rule inbound rules would have to be done on all clients.