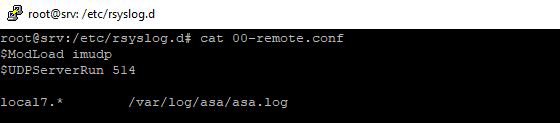
We recently replaced our Syslog Server and needed to add logging for a Firepower running ASA. Here’s a rundown on how we set it up in Ubuntu 24.04: On your Ubuntu Server: Edit the /etc/rsyslog.conf and enable UDP syslog reception. For security purposes, consider adding AllowedSender. In this case, the […]
Tips & Techniques
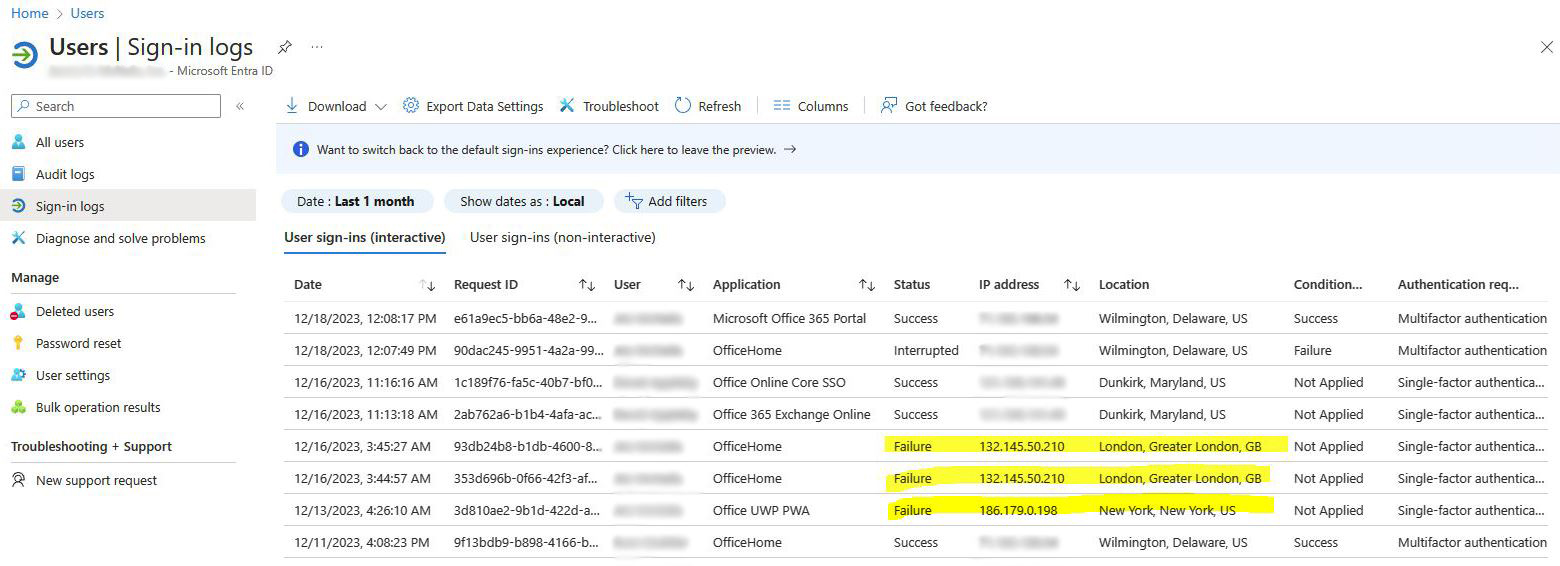
Microsoft 365 Administrators should check Sign-in logs regularly to find suspicious log-in attempts. In the example below, we do not have any users in London or New York. These are obviously attempts to hack into a user account. If any of these unrecognized log-in attempts were successful, it might indicate […]
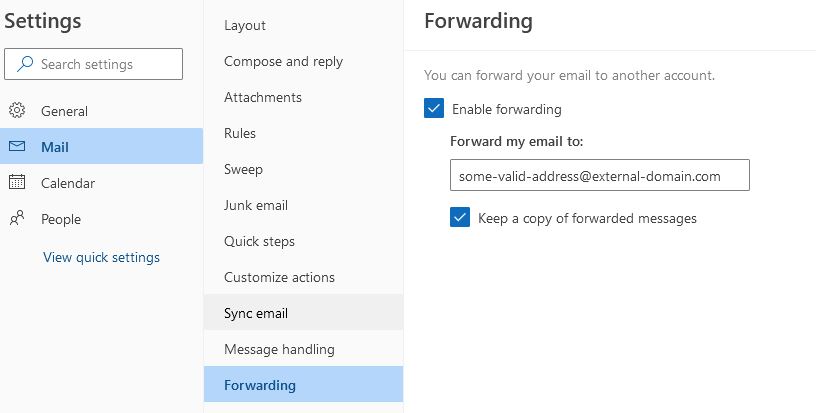
The default behavior for Microsoft 365 is to allow users to forward mail to internal recipients only. The setting “Automatic forwarding” controls this. Security > Policies & rules > Threat Policies > Anti-spam policies > Anti-spam outbound policy (Default) The problem, however, is the Outlook Web Interface will still allow […]
We recently installed a new Windows 2022 Server and joined it to a Domain. After adding it to the Domain, everything look good and the network was identified as Domain as it should. Upon reboot, it was no longer identified as being on a Domain network and fell back to […]
I recently upgraded an Ubuntu 14.04 Server to 16.04. I immediately noticed the root mail being spammed with error e-mails as below: From: Cron Daemon [mailto:root@jack] Sent: Wednesday, March 13, 2019 4:09 PM To: root@jack Subject: Cron <root@jack> [ -x /usr/lib/php/sessionclean ] && /usr/lib/php/sessionclean /usr/lib/php/sessionclean: 37: /usr/lib/php/sessionclean: arithmetic expression: expecting […]
Suppose you want to make a copy of your existing WordPress site on a different domain name (e.g. test.domain.com). Instead, maybe you want to move your site to a different domain name (e.g. newdomain.com). This procedure assumes you have shell access to the Linux server hosting your site running Apache […]