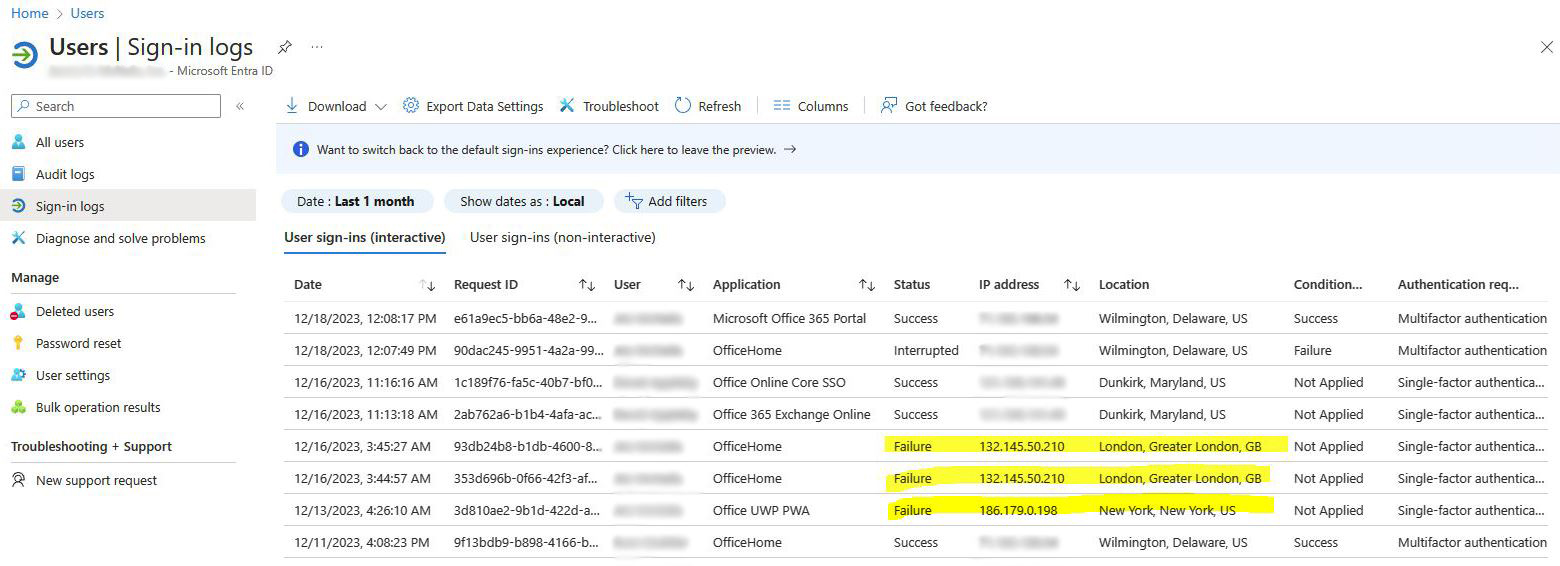
Microsoft 365 Administrators should check Sign-in logs regularly to find suspicious log-in attempts. In the example below, we do not have any users in London or New York. These are obviously attempts to hack into a user account.
If any of these unrecognized log-in attempts were successful, it might indicate that a user account has been compromised. In this case, after resetting the user’s password, the user should be signed out of all sessions.
Microsoft 365 “Security Defaults” is really not enough to protect users from being compromised. Security Defaults has no configurable items and only requires Multifactor authentication for Administrators. To enable Multifactor authentication for all users, consider using Microsoft Entra ID. Entra provides Administrators the ability to create conditional access policies with granular controls. Contact us for more information about Entra ID and securing Microsoft 365.