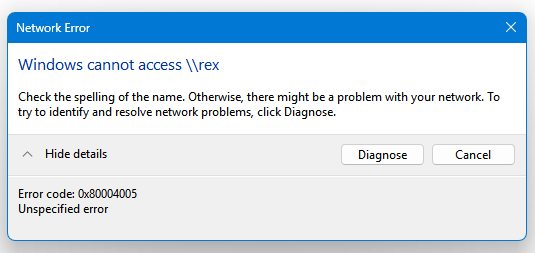
The Windows 11 24H2 Feature Update now requires SMB signing by default. This may break access to shared folders that do not have SMB signing enabled. This problem may impact older Network Attached Storage devices and some SMB shares on Linux machines depending on how they’re configured. More info here: […]
Alerts
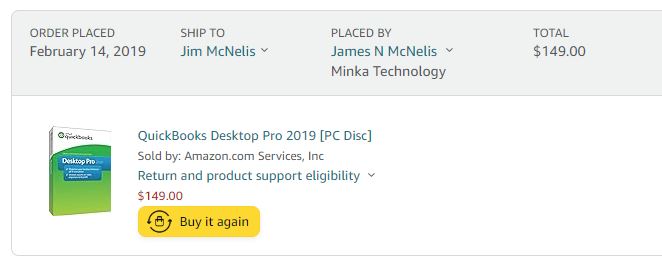
Intuit has recently announced it will no longer be selling new subscriptions of the less expensive Desktop versions of QuickBooks (Pro Plus, Premier Plus, Mac Plus, & Enhanced Payroll) after July 31, 2024. Existing subscriptions are not impacted. What does this mean? If you have a subscription, they will continue […]
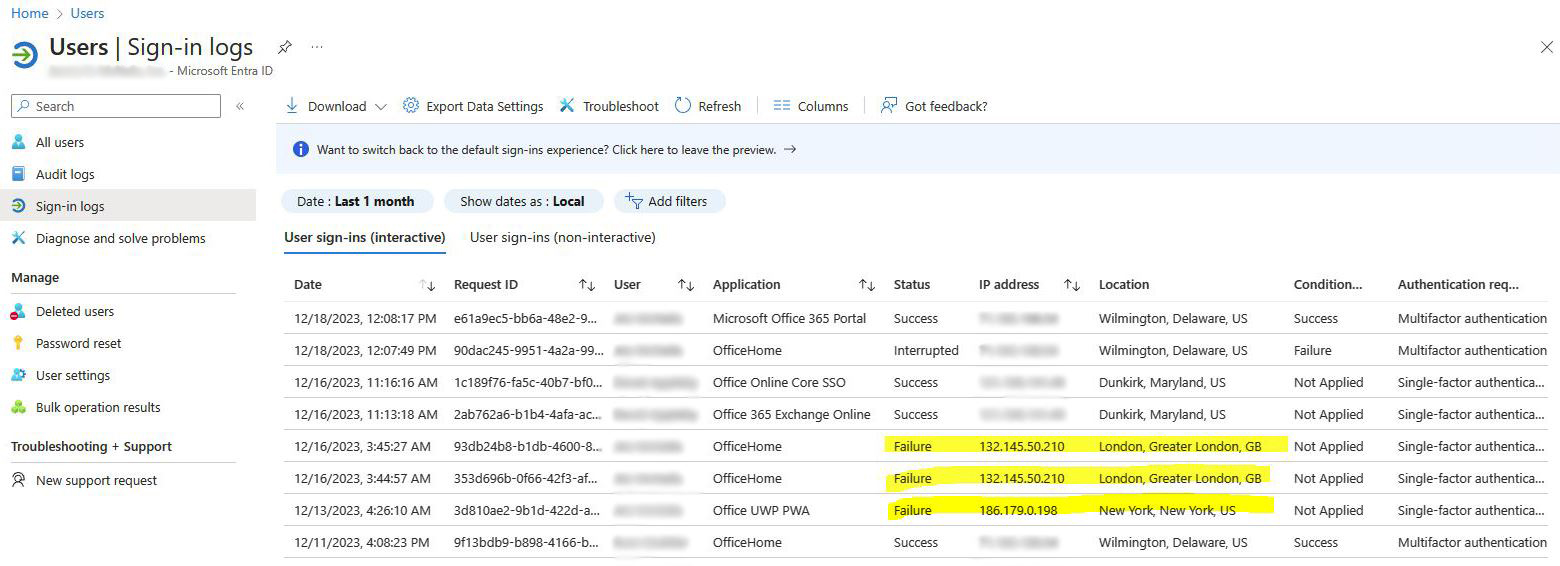
Microsoft 365 Administrators should check Sign-in logs regularly to find suspicious log-in attempts. In the example below, we do not have any users in London or New York. These are obviously attempts to hack into a user account. If any of these unrecognized log-in attempts were successful, it might indicate […]
Since Windows Updates were released Tuesday, we’re receiving an increasing number of calls from customers who are unable to print. So far, in all cases, the printers are shared from a server in a non-domain environment. Uninstalling 2021-10 Cumulative Update for Windows 10 resolves the issue (KB5006670). After uninstalling KB5006670, […]
In the past 24 hours, I’m among many who started getting no results from Windows Search. Type anything into the search box, and nothing loads. I can’t even type a command. I tried everything in the Microsoft support document Fix problems in Windows Search to no avail. Plenty of other […]
Microsoft recently announced that Small and midsize businesses will be able to purchase continued security support beyond the January 2020 cutoff for Windows 7. Windows 7 Extended Security Updates (ESU) will be sold to small and midsize businesses on a per-device basis through January 2023. SMBs will be able to […]