Beware of attackers trying to steal your passwords and other personal data.
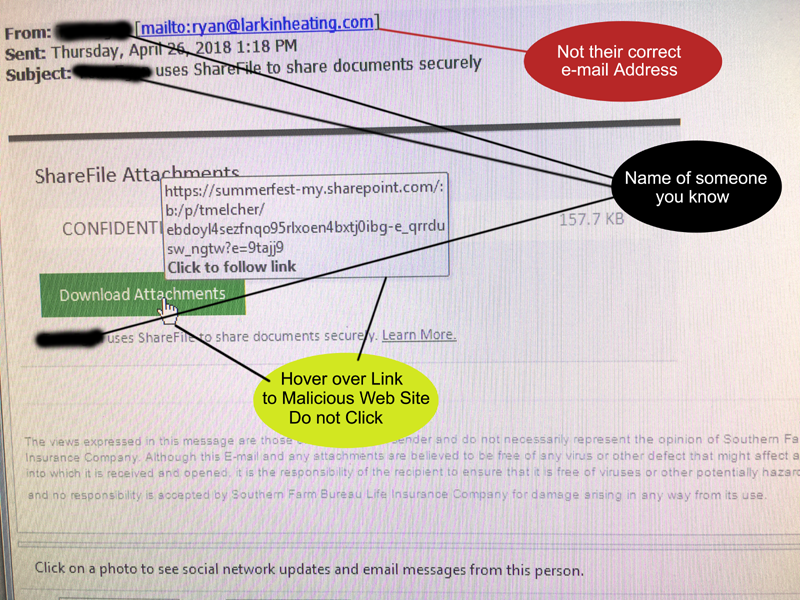
Here we can see a innocent-enough looking email saying that someone you know sent you a file securely. In our case, the email was supposedly from the recipient’s boss using ShareFile, which is a legitimate service that they often use to transfer secure documents to each other. There are some easy ways to catch malicious emails like this: Take a look at the sender’s actual email address. If it doesn’t even have the correct name, like this one, it’s likely a scam. You can also hover your mouse over the download link, but do not click. This will show you the url the link would take you to. If it doesn’t match the subject of the email, it’s likely spam.
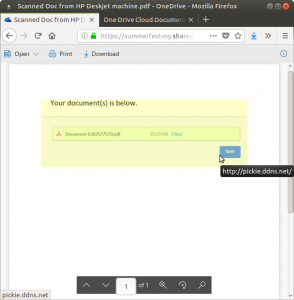
Let’s explore what would happen if a user was tricked by this email. When they click the download link, their web browser will open this webpage, showing the supposed name of a file, and an open button.
Gory Details: This page is actually a view of a pdf hosted on Microsoft Sharepoint, which is a website that no email client would blacklist. Clicking the link goes to a dynamic dns url: this allows the programmer to change it to go somewhere else whenever he wants. So if his malicious website gets taken down, he can simply make a new one and change the ddns to go there instead.
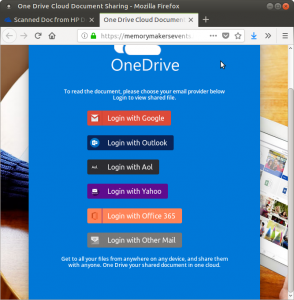
Clicking ‘Open’ request that they log in to Microsoft OneDrive. It is asking to login with one of many ways. A keen eye would notice that the url of this log in page is not a Microsoft url, so the page is illegitimate; it was faked to look like a Microsoft page.
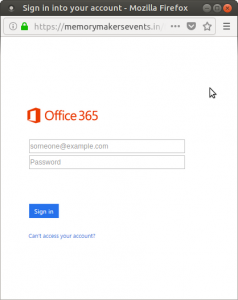
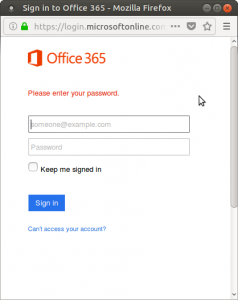
Let’s suppose that they try to sign in using Office 365. They click the link, and are taken to this page intended to look exactly like the official login page. We can again still see the URL is malicious.
Now they put in their email and password, and click ‘Sign in’. What happens? It forwards them to the actual Office 365 login page! This page looks almost identical, but we can see it’s at the official URL this time. The intent is to trick the user into thinking that they just mistyped their password, and once they try again on the official page, they get into their account and don’t even realize that they just gave their password away.
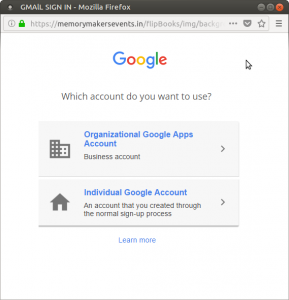
What if they had tried to login with Google instead? It comes up with a replica of the Google login process: first they choose organization or individual, and then they are presented with a faked login screen.
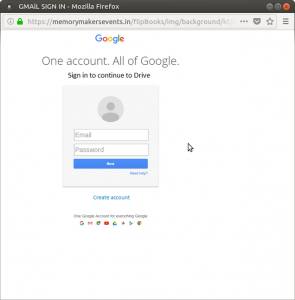
Gory Details: This login screen can easily be detected as fake. It’s not centered. The “Email” and “Password” fields are too big. Their font is wrong. You can’t click “Need Help?”, “Create Account”, or the Google logo. None of the page text is highlight-able. The reason for all this is that the page is actually just a screenshot of the login page, with the two fields and a button superimposed on top.
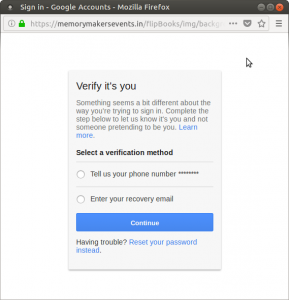
After the user gives up an email and a password, we see something interesting: they replicated Google’s “Verify it’s you” page so that they can get even more information from the user: either their phone number of email. After entering one, the user will be taken to the real login page. They might be confused, but they will not likely suspect foul play.
This is a very in-depth scam. It is injected with a real person’s name so it gets trusted by the user immediately. The first link leads to Microsoft Sharepoint so it’s trusted by the email client. It has protections against being taken down. The replica web pages are (for the most part) very well designed and look real. Finally, at the end it will redirect the user to the real login site, so they don’t suspect a thing.