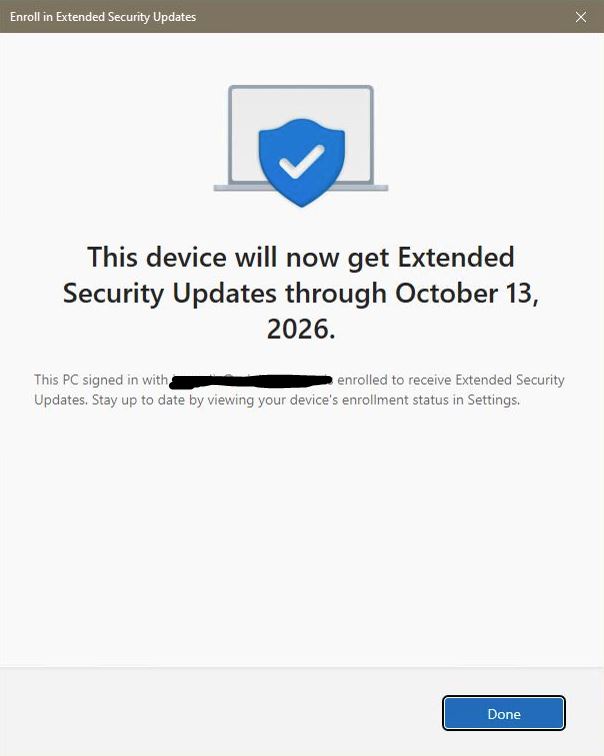
The Extended Security Updates (ESU) program for Windows 10 provides users with a more secure option to continue using their Windows 10 PCs after October 14, 2025, while they transition to Windows 11. The consumer ESU program can’t be used by commercial devices. For details, see https://www.microsoft.com/en-us/windows/extended-security-updates. You’ll need to […]
Jim
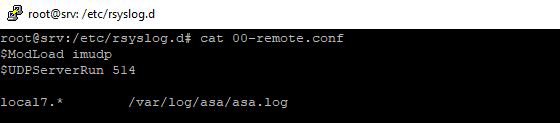
We recently replaced our Syslog Server and needed to add logging for a Firepower running ASA. Here’s a rundown on how we set it up in Ubuntu 24.04: On your Ubuntu Server: Edit the /etc/rsyslog.conf and enable UDP syslog reception. For security purposes, consider adding AllowedSender. In this case, the […]
Intuit has recently announced it will no longer be selling new subscriptions of the less expensive Desktop versions of QuickBooks (Pro Plus, Premier Plus, Mac Plus, & Enhanced Payroll) after July 31, 2024. Existing subscriptions are not impacted. What does this mean? If you have a subscription, they will continue […]
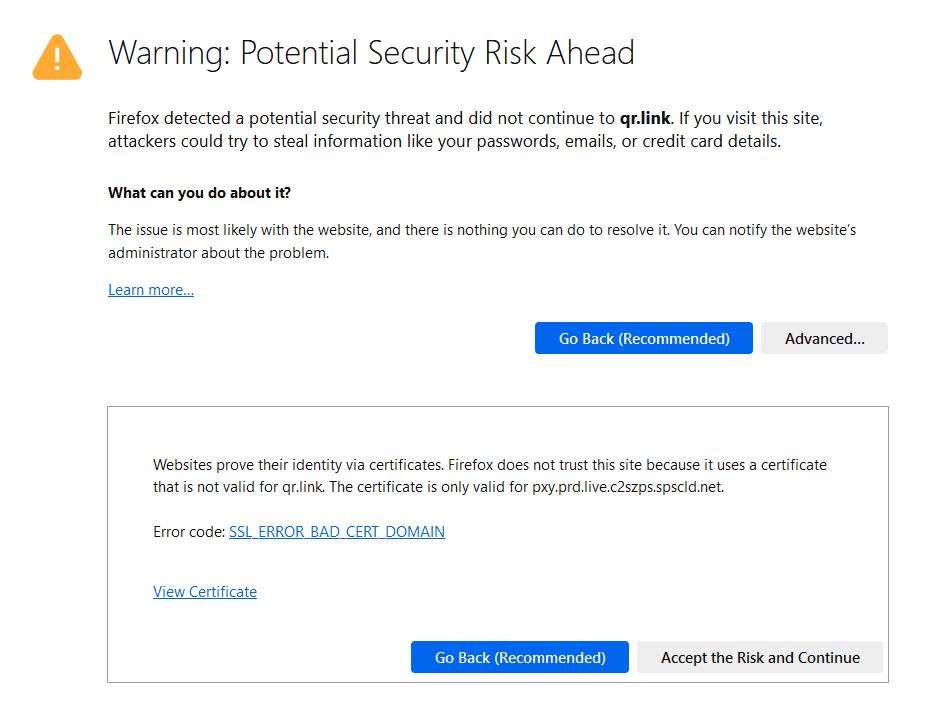
We recently ran into a strange issue at a customer location: every http/s redirect would generate a browser certificate error. In every case, the destination URL had a valid certificate. Turns out the Cisco router behind the Comcast device had an expired, self-signed certificate. Despite generating a new self-signed […]
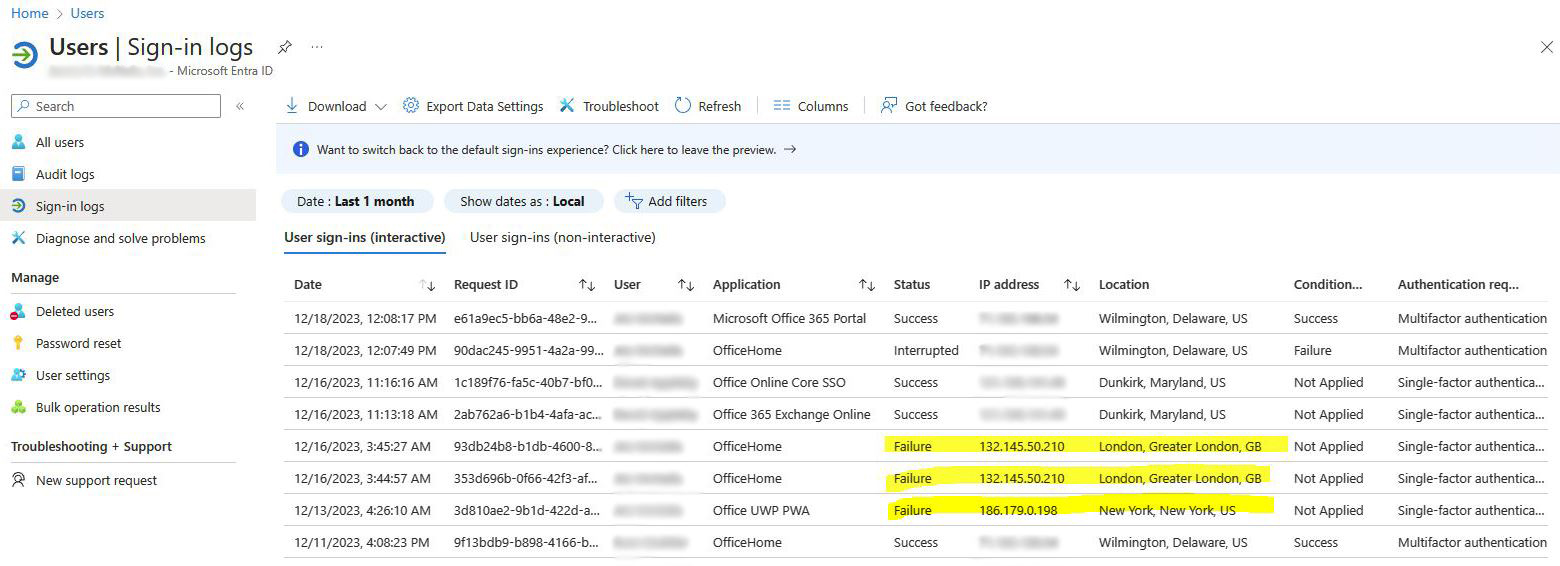
Microsoft 365 Administrators should check Sign-in logs regularly to find suspicious log-in attempts. In the example below, we do not have any users in London or New York. These are obviously attempts to hack into a user account. If any of these unrecognized log-in attempts were successful, it might indicate […]
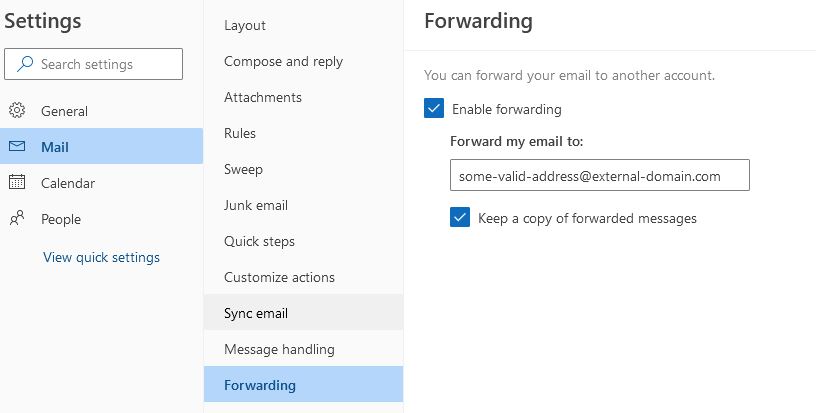
The default behavior for Microsoft 365 is to allow users to forward mail to internal recipients only. The setting “Automatic forwarding” controls this. Security > Policies & rules > Threat Policies > Anti-spam policies > Anti-spam outbound policy (Default) The problem, however, is the Outlook Web Interface will still allow […]