We recently replaced our Syslog Server and needed to add logging for a Firepower running ASA. Here’s a rundown on how we set it up in Ubuntu 24.04:
On your Ubuntu Server:
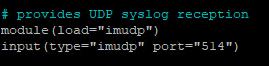
Edit the /etc/rsyslog.conf and enable UDP syslog reception.
For security purposes, consider adding AllowedSender. In this case, the IP address of your Firepower/ASA
Service rsyslog restart
mkdir /var/log/asa
touch /var/log/asa/asa.log
chown syslog:adm /var/log/asa/asa.log
chmod 640 /var/log/asa/asa.log
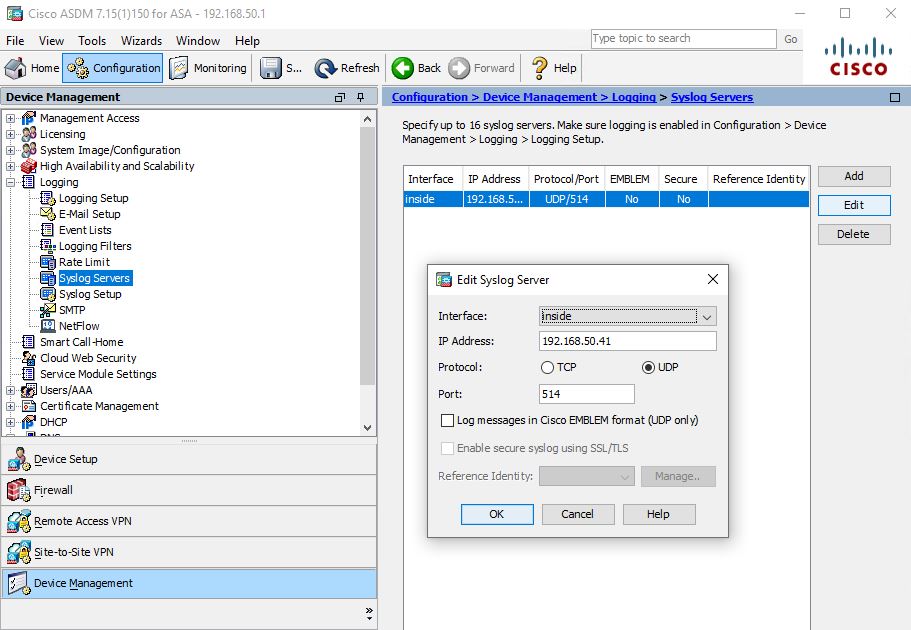
Configuring the Firepower/ASA via ASDM:
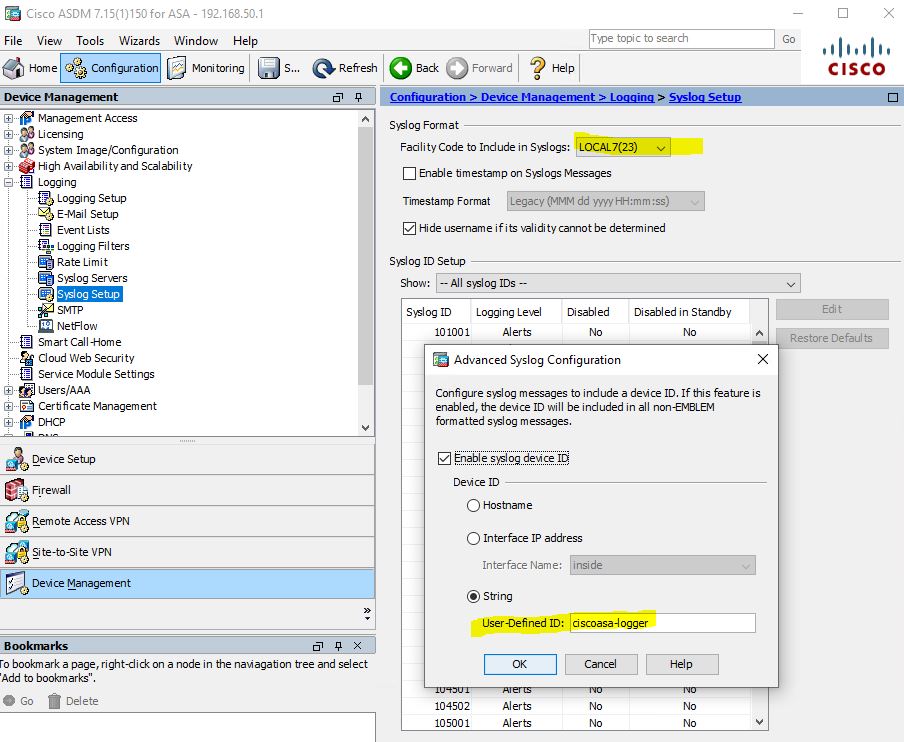
Note we used Facility Code 7. Under Advanced Settings, add a user-defined string that will allow us to prevent the asa logs from spamming the syslog.
Back to the Ubuntu server:
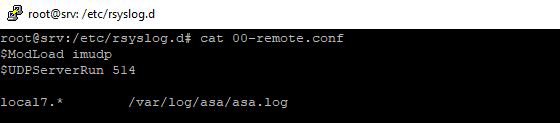
Add /etc/rsyslog.d/00-remote.conf
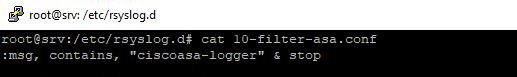
Add /etc/rsyslog.d/10-filter-asa.conf
Service rsyslog restart
You should now have the asa logs in /var/log/asa/asa.log without them also in your syslog. Note that logrotate processes files in alphabetical order. The order is important since all of this happens prior to 50-default.conf which handles the syslog and other log files.
Setup logging and rotation:
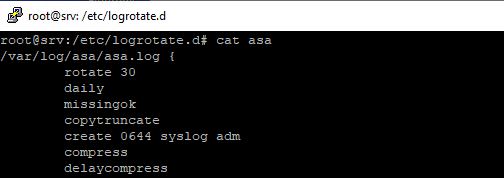
Create /etc/logrotate.d/asa
I used “copytruncate” since the log file was so active it would never rotate properly. You can test by forcing a manual rotation:
logrotate -f -v asa